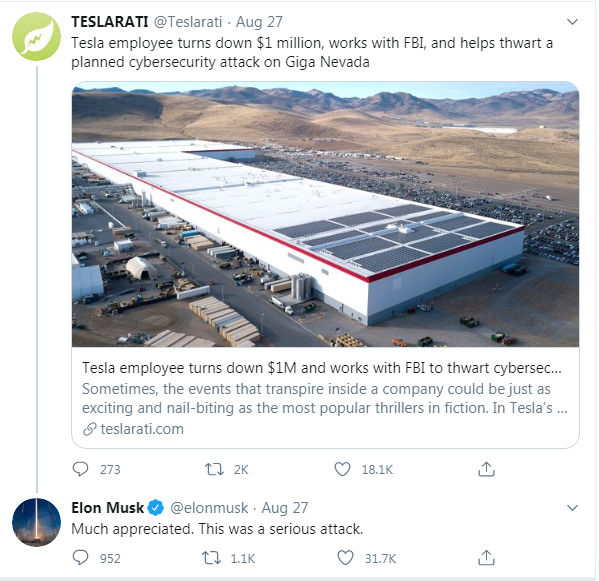
Tesla’s Elon Musk has said the company recently foiled attempts to infect its computer network with malicious software, after an employee cooperated with the FBI in an investigation. The malicious software would create an opportunity for criminals to extort money from Tesla.
Musk’s revelation comes after the United States Department of Justice (DoJ) had brought charges against a Russian national, Egor Igorevich Kriuchkov, 27. Although the U.S. government is not naming the targeted corporation in the sealed court documents, Musk in a tweet, confirms that Tesla was the intended victim of the botched attack.
According to court records, an investigation into the alleged conspiracy started after an unnamed Tesla employee informed the company of an approach by Kriuchkov. The accused reportedly asked the employee to participate in a “special project,” and in exchange, the employee would get $1 million worth of bitcoins as payment.
In return, the “executed malware would provide criminals with access to Tesla’s data. Once the data is accessed, the criminals would then “threaten to disclose this data online” unless Tesla acceded to their ransom demands. Kriuchkov and his accomplices expected to get $4 million from the botched conspiracy.
Meanwhile, after being informed of the conspiracy by Tesla, the FBI launched a sting operation to catch Kriuchkov and his accomplices. In a case replete with espionage overtones, the unnamed employee is asked to continue working with Kruichkov and his accomplices, while law enforcement agencies were building charges.
On August 17, the employee met with Kriuchkov and an unidentified accomplice. The two advised the Tesla employee of certain steps that had to be taken to ensure the successful deployment of the malware.
“Kriuchkov and the co-conspirator advised the employee that the computer used to receive the malware transmission should remain running for six to eight hours. The unidentified co-conspirator stated that once the group received access to Victim Company A (Tesla’s) data, they would execute a simulated external attack of the company,” reads the court record.
After assisting the employee to download the Tor Browser Kriuchkov then “advised the employee to set up a bitcoin wallet” using the same browser. According to the agreement, the employee would only receive his bitcoins once the task had been completed.
The FBI sting operation started sometime in late July and appears to have ended August 22.
Meanwhile, court records show that the “conspiracy intentionally cause damage to a protected computer” charges have been preferred against Kriuchkov alone. FBI special agent, Micheal J Hughes is the complainant.
What are your thoughts about the foiled malware attack? Share your thoughts in the comments section below.
Image Credits: Shutterstock, Pixabay, Wiki Commons
Disclaimer: This article is for informational purposes only. It is not a direct offer or solicitation of an offer to buy or sell, or a recommendation or endorsement of any products, services, or companies. Bitcoin.com does not provide investment, tax, legal, or accounting advice. Neither the company nor the author is responsible, directly or indirectly, for any damage or loss caused or alleged to be caused by or in connection with the use of or reliance on any content, goods or services mentioned in this article.