We all know it’s illegal to kidnap someone and ask for a ransom payment. But should it also be illegal for the victim to pay the ransom?
Earlier this month the U.S. Treasury Department did just that. It notified the world that certain ransom payments are illegal, specifically those to sanctioned ransomware operators. Should a victim pay a ransom to a sanctioned entity, that person may face a big fine.
J.P. Koning, a CoinDesk columnist, worked as an equity researcher at a Canadian brokerage firm and a financial writer at a large Canadian bank. He runs the popular Moneyness blog.
Punishing ransom victims seems heartless. But it may be one of the best ways to protect the public from extortionists. And if it wants to make a serious dent in the growing ransomware market, the Treasury Department will have to go much further than putting a few entities on its sanctions list.
On Oct. 1, the U.S. Treasury’s Office of Foreign Assets Control (OFAC) published a notice reminding everyone that several ransomware operators have been put on OFAC’s list of sanctioned entities, otherwise known as its Specially Designated Nationals (SDN) List. The agency’s letter clarifies that should a victim make a ransom payment to an OFAC-sanctioned ransomware operator, that person could be breaking the law.
The ransomware wave
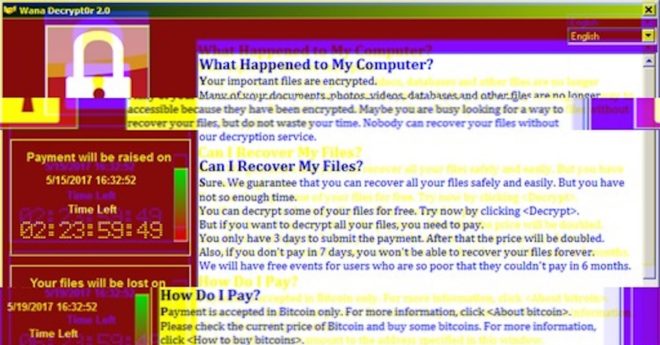
Ransomware is malicious software that blocks access to a computer system by encrypting data. Once the data is locked, the ransomware operator demands the victim pay a ransom in exchange for a decryption key.
The emergence of bitcoin, a digital, uncensorable asset, has made it particularly easy for ransomware operators to profit from their attacks. The earliest bitcoin ransomware strains targeted regular consumers with $300 or $400 ransoms. In 2019, operators like Sodinokibi, Netwalker and REvil began to move on to attacking corporations, municipal governments, school boards and hospitals.
See also: JP Koning – Bitcoin’s Ransomware Problem Won’t Go Away
The ransoms have gotten much larger. This summer, the University of Utah paid $457,059 in bitcoin for a decryption key. CWT, a travel company, paid $4.5 million to Ragnar Locker ransomware operators in July. The list of victims grows longer by the hour.
The damage involves more than just the ransom fee. Many organizations bravely refuse to give in to the ransomware operator’s demands. Rebuilding their network often costs more than the actual ransom payment. The crippled system will likely remain down for days, even weeks. The Government of Nunavut, a Canadian territory, couldn’t serve citizens for almost a month after it refused to pay Dopplemayer ransomware operators.
A collective action problem
Society’s response to ransomware is an example of a collective action problem. The public would be better off if everyone cooperated and refused to pay money to ransomware operators. With no incoming ransom income, the ransomware business would be unprofitable, attacks would cease and the collateral damage would stop.
Unfortunately, spontaneous cooperation between thousands of corporations, governments, and nonprofits is difficult to achieve. Any attempt to boycott ransom payments must rely on appeals to solidarity. But organizations will face pressure from shareholders or citizens to recover as quickly as possible, and so they will secretly pay. If 10% or 20% of victims defect from the boycott and pay the ransom, then the ransomware industry will be profitable and so everyone suffers as the blight continues.
Banning ransomware payments may not be the perfect option for stopping the growing ransomware wave, but it may be the best option we’ve got.
One way to fix the collective action problem is for the government to help push the public towards the best solution. The government can do this by declaring ransom payments illegal, and setting a penalty for rule breakers. The punishment for breaking the law would be a $20 million fine, or something like that.
Now when a ransomware operator attacks, all the victims cooperate by default. “No, we can’t pay you. If we do, we’ll have to pay an even larger fee to the government.” Ransom payments will stop, ransomware operators will cease their attacks and the damage ends.
The market for bribes as an analogy
Using the government to arrive at the best solution to a collective action problem isn’t without precedent. Another type of shady payment, the payment of bribes, provides a useful analogy.
If companies must habitually bribe foreign government officials for contracts, then that drives up the costs of doing business. The public would be better off if everyone refused to pay a bribe. But cooperation is difficult.
Until the 1970s and 80s, foreign bribes were valid tax deductions in many countries. But efforts like the U.S.’s Foreign Corrupt Practices Act of 1977 (FCAP) made it unlawful to bribe foreign government officials. Multinationals can now push back against bribery requests by pointing to FCAP. This helps push society arrive at the no-bribe solution.
The U.S. Treasury’s recent clarification about the illegality of certain ransom payments only goes part of the way. It prohibits payments to a few bad actors, but there are many ransomware operators that do not appear on OFAC’s SDN list. To help solve the collective action problem, OFAC would have to be more proactive in designating ransomware operators.
Sussing out the names and identities of all the producers and distributors of ransomware seems like an impossible task, however. It would be much easier to declare a blanket ban on all ransomware payments, just as how FCAP bans bribery. Ransom bans aren’t without precedent. In response to a wave of kidnappings by organized crime, Italy prohibited ransom payments in 1991. Colombia and Switzerland have also made ransom payments illegal. The Group of Seven has a long-standing policy of refusing to pay ransoms for hostages of terrorist groups.
The knock against prohibiting either bribes or ransom payments is that it forces the market to become more opaque. If it is legal to make a bribe, then the bribe payer can report the bribe taker. This serves to limit the market for bribes. Ban bribes and the bribe payer is incentivized to cooperate with the bribe taker to keep things secret.
This is why Kaushik Basu, the former chief economist at the World Bank, has long advocated for legalizing bribe payments.
As for ransomware, victims who pay a ransom can report the attack to law enforcement agencies like the Federal Bureau of Investigation without fearing a fine. This allows the FBI to follow up. But if it is illegal to pay a ransom, then victims that choose to pay will keep their actions a secret. Lacking accurate data, the FBI will do a poorer job of defending against ransomware.
The other knock against banning ransomware payments is the perceived inhumanity of it. Try telling a mother or father that it is illegal for them to pay a ransom to free their kidnapped child. The same goes for ransomware. A school board that has been crippled by ransomware can immediately resume classes by paying a $20,000 bitcoin ransom. But under a prohibition, children may have to go a week or two without classes as the school board rebuilds its systems.
There are also civil liberties concerns. Businesses will argue that a ban on ransoms infringes on their ability to control their property.
Bitcoin isn’t Green Dot
When extortionists find profitable ways to bilk the public, one way to fight them is to make changes to the underlying payments platform that the scammers are using. Internal Revenue Service scammers converged on Green Dot MoneyPak cards in the mid 2010s as a useful way to extort innocent Americans. The chosen solution wasn’t to tell victims that paying ransom was illegal. Rather, Green Dot Bank pulled the product for a year and reprogrammed it. And it worked. Criminals have moved on from using MoneyPaks to do IRS scams.
Unlike MoneyPaks, bitcoin can’t be reprogrammed. That leaves society with one less option for protecting itself from ransomware attacks. And so the “no payment” solution to the collective action problem beckons. Banning ransomware payments may not be the perfect option for stopping the growing ransomware wave, but it may be the best option we’ve got.