For many years now, the media periodically reports news regarding the alleged mischiefs pinned on the North Korean hackers that are seemingly detriment to target fintech businesses. But this fact seems quite odd, considering that the International Telecommunication Union estimated that the actual percentage of the population of the Democratic People’s Republic of Korea using the internet is close to zero.
Definitively, it is an environment not favorable for nourishing the skills and ambitions neither of vicious cyber-criminals nor honest cyber-entrepreneurs. However, the North Korean case shows how cryptocurrencies — born as nationality-neutral and government-free — could be twisted to become a strategic weapon, alongside more traditional instruments used in the power struggle among countries.
A tale of two countries
The gap that divides the North from South Korea, which is also considering cryptocurrencies and blockchain industry, is seemingly vast. All of the Korean peninsula shares the same language, ethnicity and culture. However, it was split in two as the result of a devastating war.
Related: Legit Vs. Illicit Crypto: North and South Korean Approaches Compared
Since then, the southern Republic of Korea entered a path of development that brought it to first achieve free-market economic prosperity and then a full-fledged democracy. More recently, South Korea became one of the countries leading the blockchain revolution, showing an innovative approach in fields spreading from technology to regulation. Meanwhile, the North remains one of the last communist countries in the world, iron-fist ruled by the Mount Paektu Bloodline and its present leader Kim Jong Un, who is a direct descendant of the regime’s founder.
The DPRK’s regime aims to monitor all communications with the rest of the world, and this attitude affects its approach to information technology as well. Data about this country is usually scattered and hardly updated; however, all the sources seem to confirm the image of a technological infrastructure that is both underdeveloped and strictly controlled by the central power.
Access to the internet is restricted to a small privileged elite, which, thanks to its bonds with the regime, could also enjoy legal or illegally imported up-to-date devices and software. It is possible to recognize a similar profile in the few North Korean internet users settled in foreign countries — such as China or India — who have direct access to upper-level local resources.
As a result, it is plausible to read all the North Korean presence in the crypto-world — or, more broadly, on the internet — as a direct offspring of central government policy or, at least, as initiatives that enjoy central power’s support.
License to hack
To understand how the North Korean is an “anomaly,” the fact that the DPRK has never normalized its relations with the rest of the world — and specifically, with the United States — should be taken into account. Moreover, since 1992, the U.S. has imposed multiple sanctions on the DPRK in the attempt to force the North Korean authorities to abandon their military nuclear program and the related missile proliferation activities.
In 2006, the United Nations Security Council reacted to the DPRK’s first atomic weapons test by passing some resolutions aimed to prevent both imports and exports to North Korea by any U.N. member state. The intense — and very likely government-sponsored — North Korean hacking activity is, then, both a weapon aiming to generate pressure on the opponent counties and a means of gathering economic resources.
The direct connection between cyber-warfare and economic sanctions may seem quite linear. Experts reported North Korean have used distributed denial-of-service attacks (DDoS) against South Korean targets since July 2009, while, during the following year, hackers focused on the banking industry and international entities. For example, Sony Pictures Entertainment was attacked in 2014 and then North Korea almost cyber-robbed the Central Bank of Bangladesh in 2016.
Since 2017, the U.S. government labels the malicious cyber activity supposedly sponsored by the DPRK as Hidden Cobra and closely monitors the hacking attempts. By that time, North Korean hackers became involved with the crypto community for the first time.
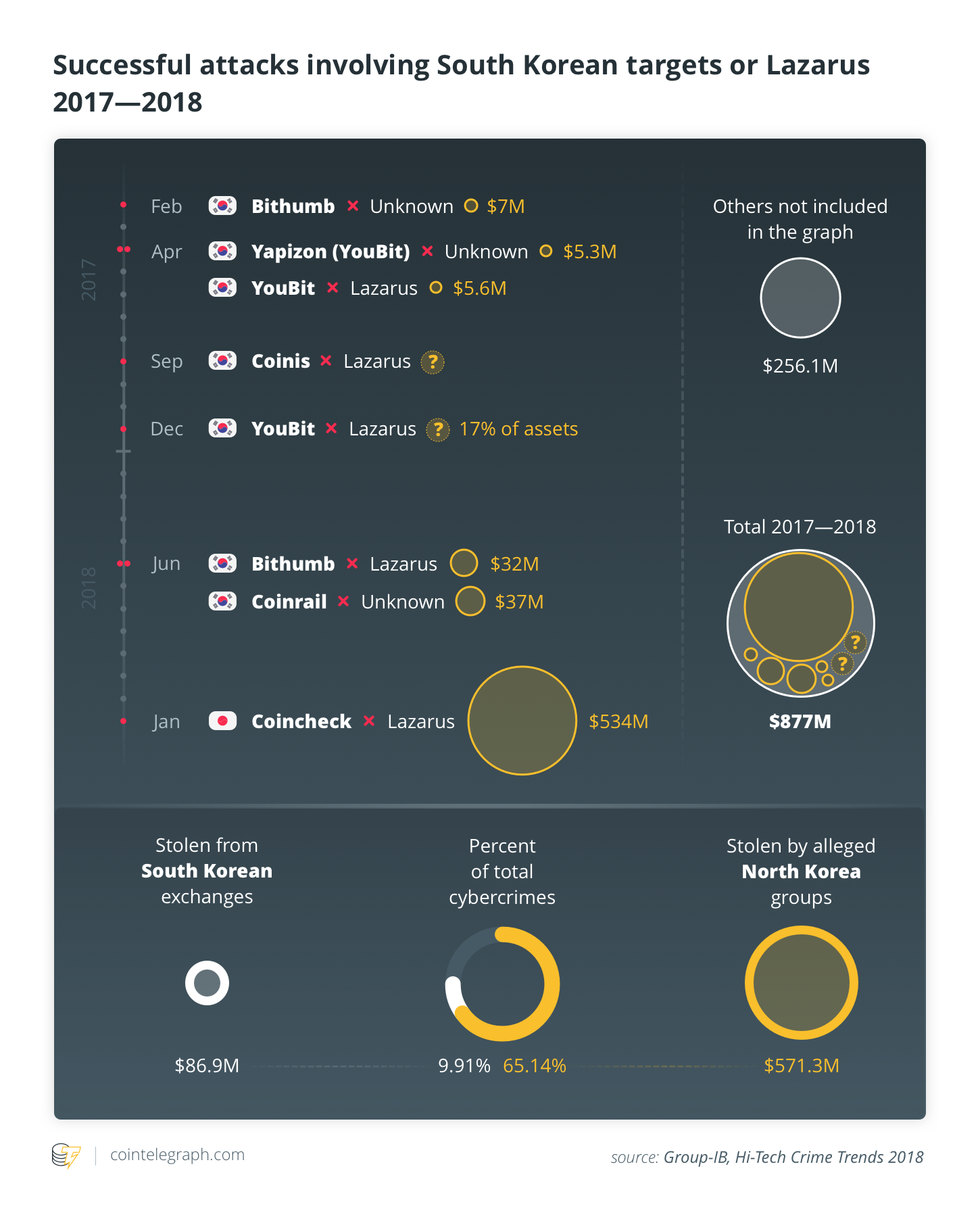
Media first reported suspicions about the involvement of the North Korean espionage structure in the security breach of the South Korean exchange Bithumb, with the theft of about $7 million in cryptocurrency, which took place in February 2017.
In May 2017, the infamous ransomware labeled WannaCry hit thousands of computers in 150 countries. Despite some sources connecting the malware to Chinese hackers, the White House officially attributed the cyberattack to the North Korean regime in December 2017.
After the ransomware campaign, since Summer 2017, North Korean hackers seemed to intensify their activity against South Korean fintech industry, raising the concern of the Korea Internet and Security Agency (KISA). Despite this, cybercriminals allegedly supported by the DPRK successfully performed other large-scale exchange heists in December 2017, hitting the south Korean services Youbit, stealing one-fifth of user funds and, in doing so, brought the company to bankruptcy.
Related: Round-Up of Crypto Exchange Hacks So Far in 2019 — How Can They Be Stopped?
Other significant breaches involved South Korean companies during the following months, even if attribution to North Korean groups was not always clear. For instance, the perpetrators of the Coinrail breach, in which around $40 million in crypto was stolen in June 2018, remained anonymous. Bithumb was hit again in March 2019, with around $19 million going missing. However, it is still unclear whether this was an inside job or if the culprits were connected with the DPRK. South Korean security experts are otherwise quite positive that the DPRK was behind the phishing campaign that targeted UPbit during May of 2019.
As the ascription of each hit is always dubious, an estimate of the loot gathered by North Korean hackers is far from certain. The U.N. Security Council’s documents that were leaked in March 2019 calculated that DPRK-sponsored hacking activity from 2015 to 2018 amassed about $670 million. A more recent report from the same source accounts claims that $2 billion in crypto was stolen by North Korean hackers from banks and crypto exchanges, which comes to 7% of the annual GDP of the country. The U.N. is presently investigating 35 attacks involving 17 countries, although most are linked to South Korean targets.
Lazarus get up and walk (possibly to jail)
In the last months of 2017, experts from the security research firm FireEye already noticed that the North Korean-sponsored attacks recorded during that year showed distinctive features compared with the previous activity. FireEye’s report interpreted the choice to target private wallets and crypto exchanges as a likely “means of evading sanctions and obtaining hard currencies to fund the regime.”
It was a direct consequence of the rising fiat-vs.-crypto exchange rates on the market, and the report concluded that “it should be no surprise that cryptocurrencies, as an emerging asset class, are becoming a target of interest by a regime that operates in many ways like a criminal enterprise.”
The operating strategy of the hackers relied on spear phishing, an attack targeting private emails address of employees at digital currency exchanges, using fake messages to deploy malware, which allowed hackers to take control of the IT infrastructure of a company.
Analysis carried on during into 2018 and connected many of the attacks to a single group, identifying itself as Lazarus (aka DarkSeol). Cybercrime company Group-IB attributed about 65% of the value stolen from crypto exchanges from the beginning of 2017 to the end of 2018 to Lazarus. The main share of the assets seized by Lazarus — $534 million of the $571 million — came from a single cyber-robbery, the security breach of the Japanese exchange Coincheck, in January 2018.
The extensive report on Lazarus produced by Group-IB discloses the connection between the group and IP addresses referring to North Korea’s highest military body. The security company states that Lazarus is likely a branch of Bureau 121, a division of the Reconnaissance General Bureau, a DPRK intelligence agency. Its activity presumably dates back to 2016.
Group-IB’s analysts detected a very sophisticated strategy based on selective attacks and the implementation of a malicious multilayer server structure inside the compromised infrastructures. Besides this, North Korean hackers developed a modular tool set to take remote control over infected PCs. This This solution both complicates the malware detection and provides additional flexibility, whereby pieces of software could be reused or combined to target specific companies, allowing hackers to divide development activity between teams.
During the spring of 2019, the cybersecurity and antivirus company Kaspersky Lab reported an evolution of Lazarus’ toolbox, presently including both Windows and macOS malware, allowing malicious PowerShell scripts in the targeted infrastructures.
Let your mind go; let yourself be free
The true goal of the North Korean hackers is probably double-faced: On the one hand, their attacks aim to undermine the IT infrastructures of countries perceived as rivals. On another, they try to seize hard currency — or assets theoretically convertible in hard currency — outside the bounds imposed by the international community. The latter goal also explains the DPRK’s small-scale attempts of mining that South Korean sources have reported, which started in the late spring of 2017 but without consistent success.
The possibility of using crypto as a potential means to avoid international financial sanctions is indeed explored by other countries presently under economic embargo — e.g., the Iranian attempts to exploit mining and even to create an autonomous international financial transfer network. Similar ambitions backed the controversial Venezuelan Petro, while also the Russian attitude toward cryptocurrencies would be influenced by the issue of international sanctions, following the Crimean crisis.
Related: Venezuelan Petro Against US Sanctions: History and Use of the Crypto
However, despite the severe reputational damage that the association with “rogue” regimes or terrorist groups brought to cryptocurrencies, the actual usability of crypto to avoid international regulation seems, at least, dubious.
The North Korean case, for instance, shows how tortuous would be the path to transfer and convert in fiat the crypto coming from local mining or illicit activities. Besides, the actual economic results of the most infamous ransomware campaigns seems widely below their resonance in the media, all the while crypto exchanges have partnered together to prevent the conversion to fiat of the assets stolen during the most successful attacks.
Indeed, North Korean hackers appear to experience some of the hardships that affected licit crypto activities in terms of privacy and adoption. For this reason, some security experts interpreted the DPRK’s sponsored activities against the crypto industry more as a means to identify additional targets or information that could enable operations against traditional financial entities in the “fiat world,” rather than robbing crypto as the primary objective.
Despite its actual economic outcomes, the North Korean case is probably the most extreme example of a regime approaching cryptocurrencies to pursue the same advantages at a governmental level that it denies to its citizens at an individual level. No contradiction is so flagrant as that of the DPRK, where cryptocurrencies are a relevant resource developed inside the state’s arsenal while the general population lacks basic knowledge about them and even about the possibility of accessing the internet.
The predecessor of the internet, ARPANET, was developed during the 1960s, to offer a reliable means of communication within the U.S. Department of Defense in case of a nuclear war. Its evolution into a global, country-neutral and democratic infrastructure seemed hardly predictable.
On the other hand, cryptocurrencies were born out of freedom while the North Korean case clearly shows how they could become a manageable weapon in the hands of a totalitarian regime.
The institutions, society and the surrounding economic environment seem, one more time, more relevant than technological architecture to determinate the evolution path of disruptive innovation.