The cryptocurrency wallets made by Trezor have long been considered a standard of the industry and have been trusted as a reliable cold storage of cryptocurrencies by large media, blockchain developers and crypto enthusiasts worldwide. The company prides itself on the quality of its product and in being one of the leaders in the market of hardware wallets.
But it was only a matter of time before the Trezor’s flagship device got the attention of fraudsters. On Nov. 19, the company issued an official warning to users which reported that an almost identical copy of Trezor One was spotted in the market:
[PSA] In recent weeks we have discovered a non-genuine Trezor One devices which try to imitate the original to the bone.
For more information on how to spot a fake Trezor One device, please read our latest blog post here: https://t.co/tpe21iTVXm
— Trezor (@Trezor) November 19, 2018
“Imitation is the sincerest form of flattery”
An announcement published on Trezor’s official blog begins with this proverb. Though the company’s officials acknowledged that “Trezor clones have been released over the years,” a “fake Trezor device, manufactured by a different, unknown vendor” has become a “startling” discovery for them.
SatoshiLabs, a manufacturer devteam, has made considerable attempts to assure the community that the fake devices are not identical in any way to the original and have significant difference in both content and functioning capability. As explained in the “how to distinguish” guidelines in the same blog post, the real Trezor One device bears a different name and is manufactured by legitimate companies, while the fake device replicates the original’s outward appearance to fool potential buyers.
SatoshiLabs has also stated that the fake devices could be immediately spotted by their packaging, which differs from the legitimate device by the design of the special holographic markings and the presence of unsightly ‘Made in China’ markings. Though imitation may be “the sincerest form of flattery,” it is likely that the minor similarities between the devices end on outward appearances and do not extend to the software, which may well be faulty or even full of malware, in the case of the fakes.
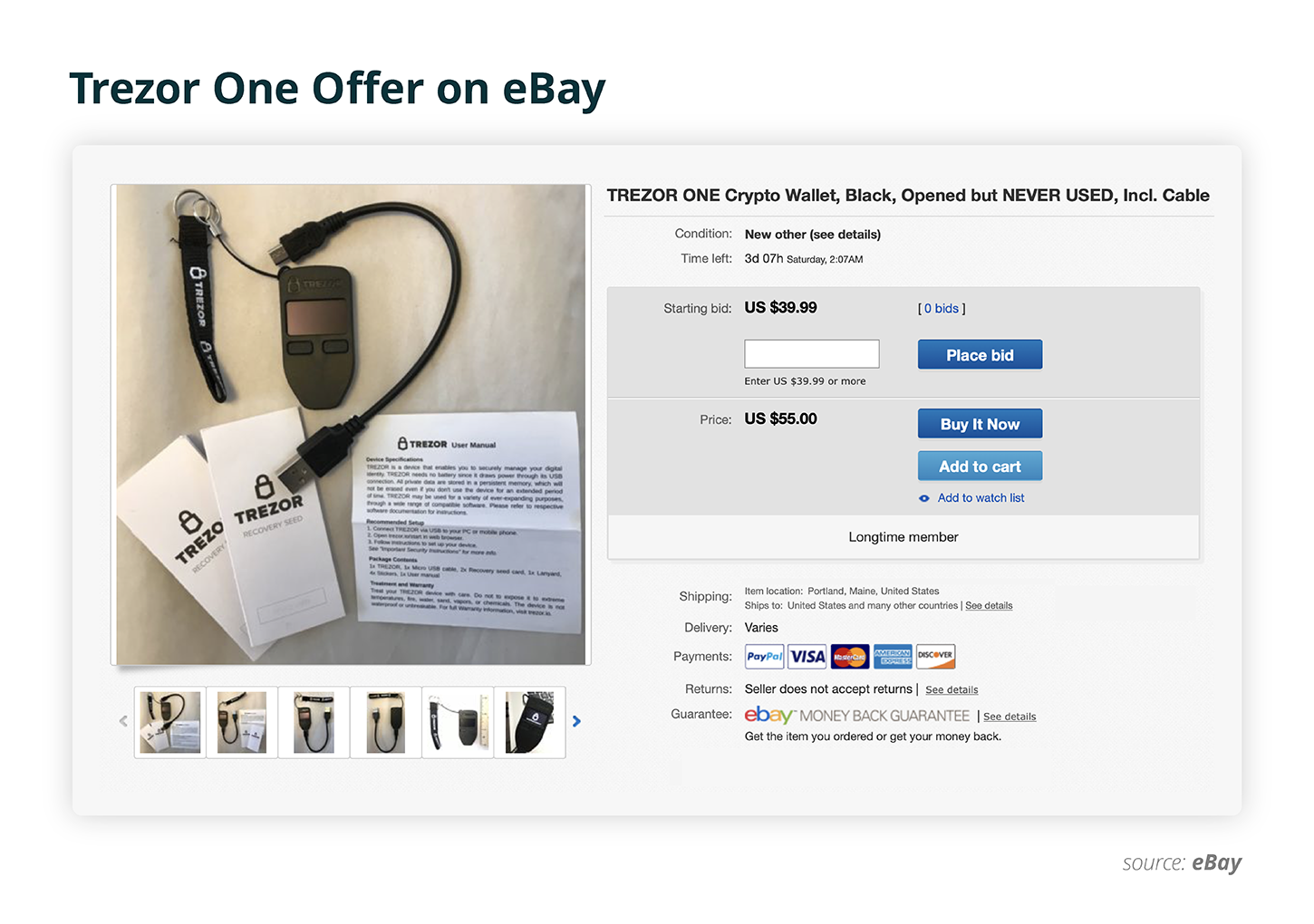
Those customers, who are used to buying electronic devices on such platforms as Amazon or eBay, could have been confronted with an offer to purchase a “used just once” or “opened but never used” Trezor One wallet. The price for such an item may vary from $39 to $49.
Cryptocurrency hardware frauds
Trezor has encountered situations of this nature before, though not the blatant copying of its product. The company has always emphasized that its software is the “most secure” and is invulnerable to hacking attacks.
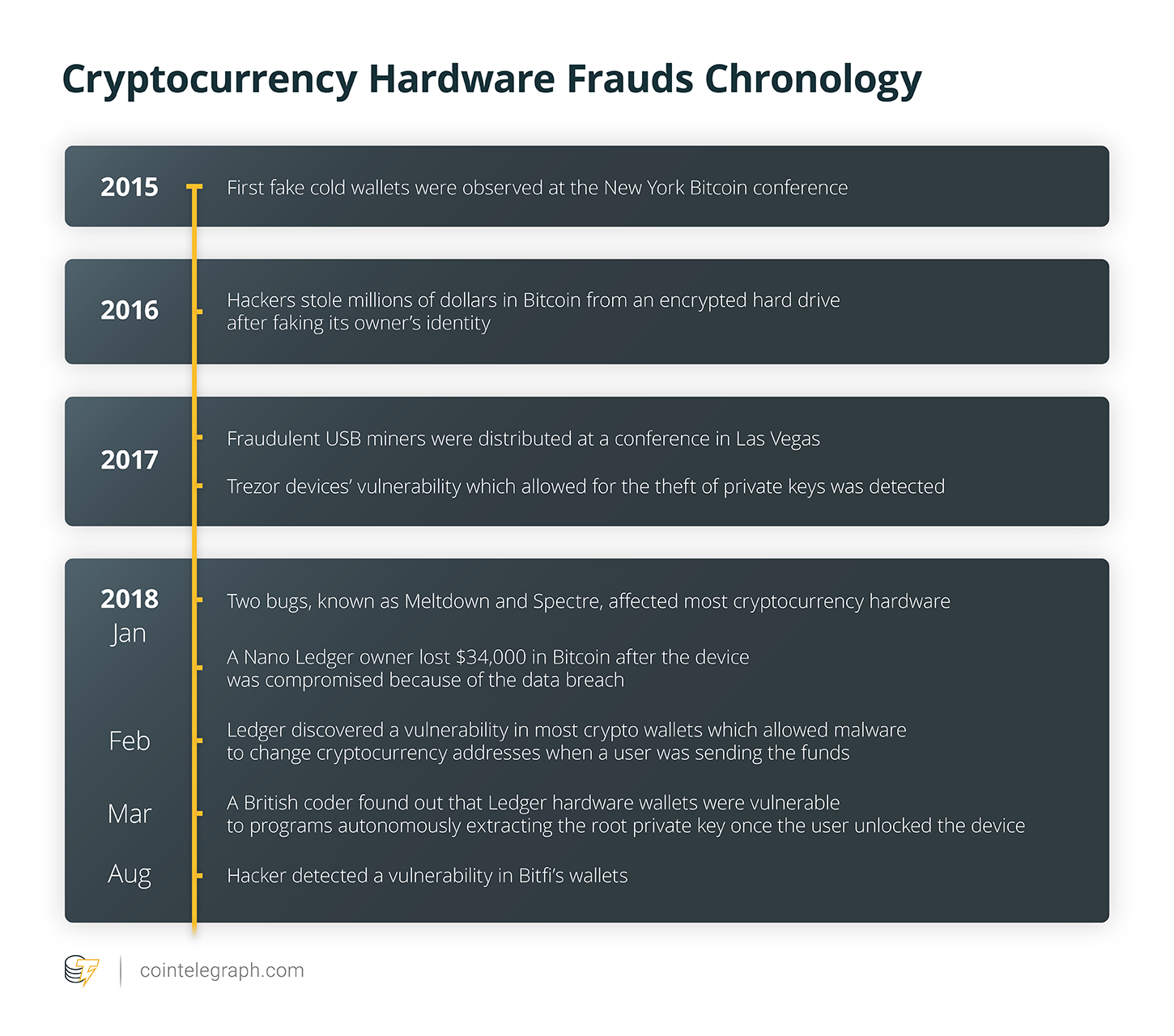
These claims were questioned when, in mid-August 2017, a group of hackers managed to crack Trezor wallets using relatively simple methods, allowing for the theft or identification of private keys from those devices. After an investigation into the incident, Trezor stated that the seed for the hacked wallet’s private key was saved on a flash memory card and relocated to the afflicted device’s random access memory (RAM) during its use. It was later identified that only Trezor wallets were affected by the vulnerability. In response to the incident, Trezor released the firmware security update version 1.5.2 on Aug. 16 and later claimed that users were safe and had nothing to fear.
The attacks were not limited to Trezor, as other devices have been also affected by bugs and bad actors. A report published by SpectreAttack in early January 2018 revealed two bugs, known as Meltdown and Spectre, which were said to exploit security vulnerabilities in Intel, AMD and ARM processors of any device they are installed in. The list of devices included PCs, laptops, tablets and smartphones.
The Meltdown bug afflicted Intel chips that were estimated to be installed in about 90 percent of all computers worldwide. The Spectre bug affected Intel, ARM and AMD chips on any device and both types of malware were reported to be capable of operating in cloud storage environments.
The Ledger Nano S, another popular hardware wallet, has also been found to be lacking in terms of security. On Feb. 5, 2017, it was discovered that users were open to attacks when connecting their Ledger Nano S to a device compromised by a hacker and using it to transfer funds between accounts on a regular basis. The fraudster could easily replicate the account addresses and gain access to the funds stored therein.
In January 2017, the participants of various Bitcoin and blockchain-related conferences were given fake Bitcoin hardware wallets imitating the legitimate products of Trezor and Ledger. Such ruses were aimed at stealing the funds that would be placed on the devices.
Earlier, in December 2016, a hacker managed to fake the identity of a user and transferred their phone number from T-Mobile to a carrier called Bandwidth, which was linked to a Google Voice account used by the attacker. The hacker then reset all the victim’s passwords and stole dozens of Bitcoins, though the exact amount wasn’t revealed.
There are numerous vulnerabilities that hackers can exploit to steal hard-earned cryptocurrencies. Notably, software companies are unaware of a large number of tricks that the hackers have up their sleeves, while the latter are developing ever more devious and elaborate schemes to phish out cryptos from their unsuspecting victims.
Six vulnerabilities of hardware wallets
In his blog, Karl Kreder, Ph.D. — the co-founder of wallet manufacturer Grid+ — outlines six vulnerabilities based on his personal and professional observations, which could potentially lead to hardware wallets being compromised or hacked.
Man-in-the-Middle (MIM) Attack
As observed by Kreder, MIM attacks can affect some cold storage devices, whose screens display eight digits of the recipient address when a user sends the funds. According to the calculations he made in August 2017, hacking into such a device could be implemented for “a relatively small economic cost” (about $800) with the use of the address generators like vante.me.
USB Device Firmware Upgrade
Wallets like Ledger and Trezor can be vulnerable when being upgraded via a USB port. This option is often allowed by a manufacturer with the help of so-called USB Device Firmware Upgrade (DFU). As reported, the market has already seen successful attempts to use DFU to remotely dump the memory of the STM32F family of microcontrollers.
This could lead to a number of negative consequences for a cold storage device owner, starting with the theft of private keys and ending with a malicious actor re-flashing the wallet with malicious code during an upgrade.
Cracking PINs
As a rule, in case the hardware device is lost or falls into the hands of a bad actor, manufacturers like Trezor and the Ledger reset the wallet if a wrong pin is entered three times. This prevents a fraudster from getting control of the wallet and using a brute-force-based attack to compromise a pin.
During the Defcon conference, the Cryptotronix developers demonstrated that the Trezor STM32F205 could be glitched by using both Vcc and clock glitching attacks. As a result, the device becomes vulnerable and private keys can be obtained by a third party without needing to know the pin.
Supply Chain
This is the sort of vulnerability being faced by Trezor One owners who bought fake copies. Originally, a Trezor hardware device is protected with branded holographic stickers and super glue which holds the housing together. This is supposed to protect the wallet from being tampered with after it was sent by the manufacturer to a customer. However, if the device falls into a fraudster’s hands, the latter can flash a malicious version of the software or re-insert the key. Once this is done, the device’s body is sealed with a similar holographic sticker and glue.
Recovery Phrase
The author considers a recovery phrase to be “the most vulnerable piece of the security puzzle,” since this 12–24 word series string usually consists of plain text and is often stored “in a sock drawer at one point.”
Surveillance
As warned by Edward Snowden, PINs and passwords can be obtained by a spying fraudster spying via an ordinary desktop or smartphone web camera. Cryptocurrencies holders and traders may not be an exception.
Community’s reaction
The community responded to the news about faked Trezor One devices with a mix of outrage and frustration peppered by some understanding. Some pointed to the pathetic security measures taken by Trezor in relying on a holographic sticker as a safety barrier. Others confirmed they bought fake Trezor wallets.
I can confirm. I bought 2 on Amazon several months ago, and they have the wrong holographic seal. Never opened them. pic.twitter.com/Emq8ugxIMo
— Brooke (@bitcoinmom) November 19, 2018
Many responsible users commented with calls for vigilance and additional security measures, while opinion leaders remained sided with the legitimate manufacturer. Naturally, a flurry of recommendations and comments ensued as users offered various tips on how to keep their wallets safe — with suggestions ranging from keeping the wallets under a mattress with a shotgun nearby to leaving the crypto market for good.
“If you don’t own your private keys, you don’t own your coins”
The faking of devices occupying a market worth about $95 million in 2017 alone was only a matter of time, as it was predicted earlier by some crypto enthusiasts.
Though the fake software may not be suitable for crypto storage in the first place, the price difference may be enough to lure unsuspecting users and lead to woe and losses of their funds. Given the fact that today, the majority of cryptocurrencies are held in cold storage, and 97 percent of exchanges prefer to keep the funds this way, the forgery of devices for crypto storage may still remain attractive for fraudsters, according to a study issued by the University of Cambridge.
The experts and the manufacturer itself recommend maintaining vigilance when selecting hardware wallets and to purchase them only from verified resellers that can be found in a list on the official Trezor website.
Hello Rahul, the main differences are the hologram and barcode on the back of the box. The fake Trezor could be using our firmware, so it is best not to use it. The safest is to buy Trezor from our official shop or resellers.
— Trezor (@Trezor) November 20, 2018
Apart from the main warning given here and there by Trezor – “If you don’t own your private keys, you don’t own your coins” — some experts advise having two cold wallets and not to keep all the funds in one place to diversify the risks.
Companies, in their turn, should use their leverage to attempt to stop the imitation of their products through legal channels and to implement additional security measures after extensive analysis of the fake devices, as the community believes.