We were graced with one more typical “degen yield farm” popping in and out of relevance this week.
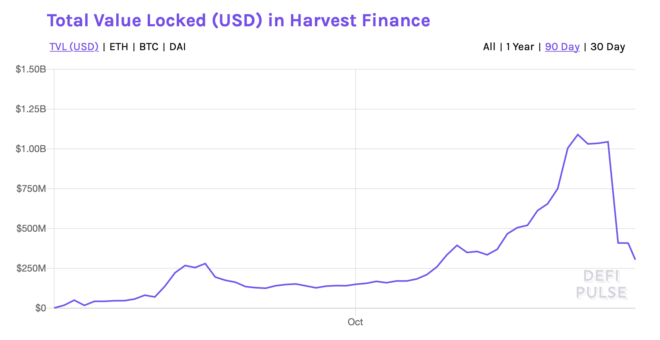
Harvest Finance collected as much as $1 billion in total value locked before an “economic exploit” sent it tumbling down. Its value locked measure now hovering around $300 million and prospects for a recovery looking bleak.
The exploit has once again reignited debates among DeFi community members as to whether these types of flash loan-based arbitrage attacks are actually hacks.
Harvest features yield farming vaults similar to Yearn’s. They issue tokenized vault shares based on the value of the assets supplied by users. Some of these vaults rely on Curve’s Y pool, which powers liquidity for swaps between USDT, USDC, DAI and TUSD.
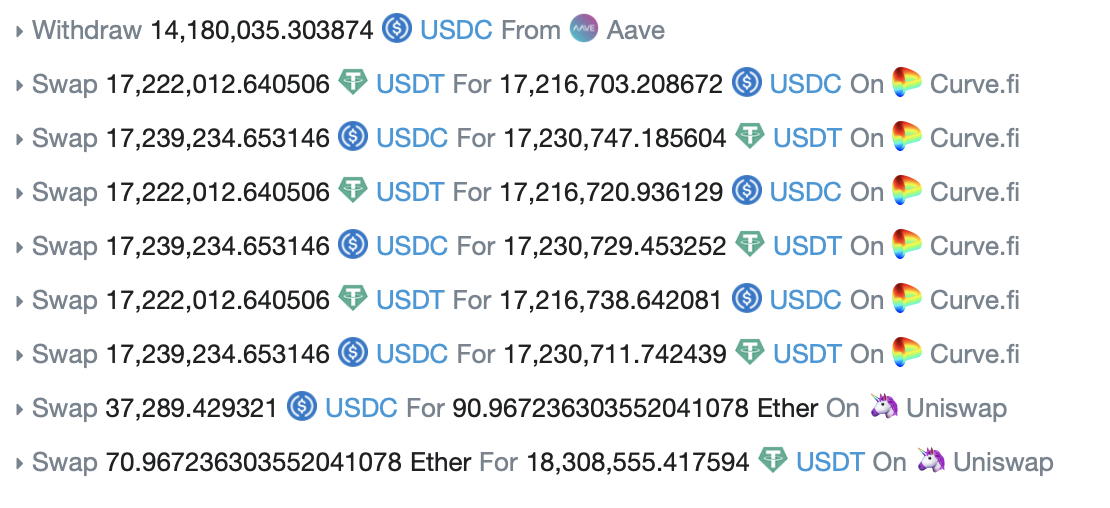
The attack used flash loans to convert $17 million USDT into USDC through Curve, temporarily boosting the USDC price to $1.01. The attacker then used another flash-loaned stash of some $50 million USDC — which the system considered to be worth $50.5 million — to enter the Harvest USDC vault.
After entering, the attacker would reverse the previous USDC trade back into USDT to bring the price in balance, and then immediately redeem their shares of Harvest’s pools to receive $50.5 million in USDC — a net profit of $500,000 per cycle repeated enough times to obtain $24 million in loot.
So is this a hack or not?
Technically, there were no vulnerabilities involved here. There was a bypassed check for these types of “arbitrage trades” that detects if the price of these stablecoins deviates too much from their intended value. But it was already set quite low and it’s really more of a mild inconvenience than an actual blocker — an attacker just needs to use more exploitation cycles.
So in that sense, proponents of the theory that this is just an arbitrage trade are correct — there is no unintended behavior in the code, it’s more like weaponized market manipulation repeated at speed.
The Harvest Finance team nevertheless assumed responsibility for this as a design flaw, which is commendable.
Honestly, I’m not even sure what the point of these semantic debates is. People lost money in a preventable way. An audit should’ve caught this and marked it as a critical issue.
But there’s definitely a case to be made that it’s a different category from bugs like reentrancy. It highlights that these financial building blocks — often referred to as “money Lego” — must be designed with utmost care at the drawing board.
It’s like if somebody created a gun out of Lego parts and people were debating if the gun was “created” or “discovered” because the parts were technically assembled as designed. Either way the Lego parts should be reworked so that they can’t become a lethal weapon.
A bit too much trust for crypto standards
Before the hack, Harvest was notable for its extreme degree of centralization. In its glory days, all of the $1 billion could’ve been stolen by a single address, most likely controlled by the anonymous team behind the project. A couple of audits highlighted that fact, also making it clear that the address was able to nominate minters and create tokens at will.
Fans of the project vigorously defended it, saying that because of the time lock, the governance key holders could only steal the money 12 hours after signaling their intentions, or that they could only print a limited number of tokens.
I’ll let you be the judge of those arguments. The wider point is that in the search for yield, these “degens” are ignoring the basic tenets of decentralization and, you know, what DeFi is about.
And I’m not saying it’s bad because of some idealistic principles I have. It’s because of rug pulls. These are the exact circumstances that led to disasters like UniCats.
The crazy story of bZX
Speaking of hacks, I had the pleasure of interviewing the bZX team about their terrible year. They suffered a total of three hacks over 2020, although some of these definitely feel more like the “economic exploits” mentioned earlier.
The team is nothing if not dedicated. One story that didn’t make it to the article was how Kyle Kistner jumped a fence in the middle of the night and broke into the gated community where his co-founder Tom Bean lived. There was apparently a bug that needed to be fixed literally as soon as possible.
Judging from the story, being a DeFi developer is not for the faint of heart, nor for people who like to sleep.
Of course, one can’t help but notice that bZX was exploited a bit too often. As a former bug bounty hunter I could definitely see how their security practices were sub-par earlier in the year — the bug bounty program was pretty bad, for example — but I also saw how they rectified many of their mistakes. Maybe there are other underlying issues, but I think they could eventually bounce back if no more incidents occur.
The DeFi threat to staking
A ConsenSys report highlights an issue that has kind of been ignored so far, which is essentially the opportunity cost of staking in a DeFi environment.
The idea is pretty simple: money chases the highest yields, and DeFi seems to be offering plenty of them these days. Even something relatively tame like 20% APY could beat the potential 8% or so from staking and validating Ethereum 2.0.
That problem is compounded even more when you consider that Ethereum’s Phase 0 won’t let you withdraw or transfer the tokens you committed until Phase 1 or 2 comes. You’re basically making a bet that the team will ship a full implementation in a reasonable timeframe, and you’re not really getting rewarded that much for the risk.
In that scenario, the more popular DeFi is, the less secure the network is, and that’s a big problem.
Thankfully, it is largely solvable through staking derivatives — liquid tokens backed by collateral used for staking, a sort of Ether IOU. There are risks involved — namely that the underlying collateral could get slashed and the IOUs would be suddenly worth less. The good thing for the network is that only DeFi is affected in this case, reestablishing the natural hierarchy of importance.
But that highlights just how many unintended interactions there could be in the future. DeFi can already get extremely complex, and if people don’t fully understand it, the consequences could be terrible.